

- 日本 - 日本語
- 한국 - 한국어
- Australia/NZ - English
Asia, Pacific, and Japan
- United Kingdom - English
- DACH - Deutsch
- France - Français
- Nederland - Nederlands
- España - Español
- Italia - Italiano
Europe, Middle East, and Africa
- IT Service Management Transform service management to boost productivity and maximize ROI.
- Customer Service Management Deliver great customer service while reducing costs.
- IT Operations Management Deliver proactive digital operations with AIOps.
- Integrated Risk Management Make risk-informed decisions while improving business resilience.
- HR Service Delivery Deliver guided journeys and more efficient employee service.
- Strategic Portfolio Management Gain insights to move from strategy to business outcomes.
- IT Asset Management Optimize technology use and spend over the full IT asset lifecycle.
- Integration Hub Connect anything to the ServiceNow platform.
- Security Operations Effectively defend against security threats and attacks.
- Field Service Management Reduce field service costs and increase operational efficiency.
- Application Portfolio Management Align applications with strategy to reduce technology risks and costs.
- App Engine Deliver unique, intelligent workflows quickly and safely.

- Cloud Transformation and Enablement Plan, scale, and operate in the cloud.
- Customer Service Remove friction, reinvent service, transform experiences.
- Cyber Security and Resilience Minimize the risk, impact, and cost of securing your business.
- Employee Experience Boost self-service, automate the mundane, empower talent.
- Enterprise-wide Risk and Resilience Manage risk enterprise-wide and reduce the chaos of change.
- Facilities Management Manage, optimize, and streamline workplace operations.
- Finance and Supply Chain Unify people, processes, and systems to get work done.
- Global Business Services Optimize all shared services on a single platform.
- IT and Digital Operations Anticipate needs with efficient IT and digital operations.
- Low Code and Intelligent Automation Maximize business automation with intelligent workflows.
- Value Acceleration Increase ROI and maximize value from the ServiceNow platform.
- Education Provide exceptional student and staff experiences.
- Energy and Utilities Optimize energy and utility operations with modern workflows.
- Financial Services Future-proof your financial institution.
- Government Accelerate the mission to serve.
- Healthcare and Life Sciences Deliver better outcomes and make healthcare more human.
- Manufacturing Streamline processes across your entire manufacturing organization.
- Nonprofit Help your team work seamlessly and focus on the right things.
- Retail Digitize processes to streamline your retail operations.
- Service Providers Meet rising expectations with a flexible service provider platform.
- Telecommunications, Media, and Technology Fuel growth and lower costs for the digital economy.
- Technology workflows Automate IT operations to prevent issues and provide scalable services.
- Application Portfolio Management Align applications with strategy to reduce technology risks and costs.
- Business Continuity Management Anticipate and minimize the impact of business disruptions.
- Clinical Device Management Automate the installation and service of clinical devices.
- Cloud Cost Management Raise visibility and control cloud costs as you automate tasks.
- Enterprise Asset Management Maximize your return on enterprise assets while minimizing risk.
- ESG Management Maximize your ESG strategy, impact, and value.
- IT Asset Management Optimize technology use and spend over the full IT asset lifecycle.
- IT Operations Management Deliver proactive digital operations with AIOps.
- IT Service Management Transform service management to boost productivity and maximize ROI.
- Integrated Risk Management Make risk-informed decisions while improving business resilience.
- Operational Technology Management Protect and manage your operational technology assets.
- Security Operations Effectively defend against security threats and attacks.
- ServiceNow Cloud Observability Unify event management across cloud-native and traditional IT.
- Strategic Portfolio Management Gain insights to move from strategy to business outcomes.
- Third-party Risk Management Take control of the third-party risk lifecycle.
- Employee workflows Inspire employees with a unified experience that boosts productivity.
- HR Service Delivery Deliver guided journeys and more efficient employee service.
- Employee Growth and Development Drive productivity and growth by streamlining talent development.
- Legal Service Delivery Accelerate business outcomes through efficient legal operations.
- Workplace Service Delivery Optimize space utilization with modern workplace experiences.
- Customer workflows Anticipate customer needs and empower them with a simplified experience.
- Customer Service Management Deliver great customer service while reducing costs.
- Field Service Management Reduce field service costs and increase operational efficiency.
- Sales and Order Management Modernize your sales and order lifecycle from lead to cash.
- Creator workflows Build low- and no-code workflow apps that connect your enterprise.
- App Engine Deliver unique, intelligent workflows quickly and safely.
- Automation Engine Connect and orchestrate tasks, data, and, workflows.
- Integration Hub Connect anything to the ServiceNow platform.
- Accounts Payable Operations Streamline processes and pay with confidence and accuracy.
- Sourcing and Procurement Operations Simplify the employee purchasing experience.
- Supplier Lifecycle Operations Speed supplier onboarding and simplify engagement.




Recovery Email
Edge Encryption
Benefits of Edge Encryption
Reduce risks to sensitive data
Use integrated protection and monitoring tools that meet compliance and governance requirements.
Mitigate data leakage
Lower risks via trusted end-to-end protection for data in use, in motion, and at rest.
Minimize impact to user operations
Balance security with user needs by using encryption-level options to limit impact on users.
Features of Edge Encryption

Data encryption management
Configure fields and attachments that should be encrypted, and manage encryption keys and rules.

Mass key rotation
Re-encrypt data automatically with new default encryption keys to ensure record protection.

Tokenization
Protect targeted data patterns within a field while leaving all other data in that field unaffected.
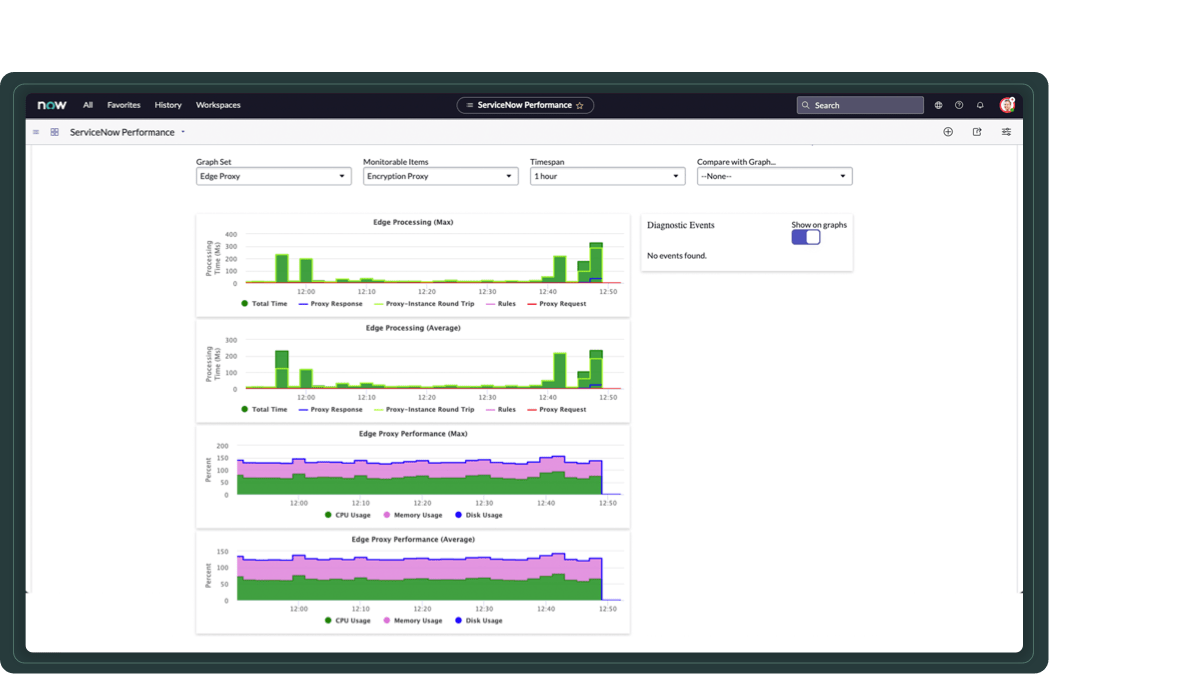
Monitoring tools
Monitor the Edge Encryption proxy server action, and use logs to troubleshoot end-to-end activity.
Additional features
Enterprise-grade performance and resilience
Support standard network load balancers to deliver and scale reliable performance and availability.
Customer retained encryption key administration
Manage your encryption key environment to meet compliance requirements and fully secure your data.
Resources

